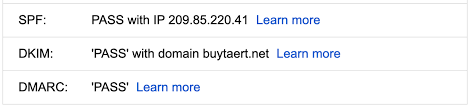
DMARC, SPF, and DKIM: The Foundations of Email Authentication
Email remains one of the most vital communication tools for businesses and individuals. Unfortunately, it’s also a favorite attack vector for cybercriminals, with phishing, spoofing, and email fraud becoming increasingly…