Email continues to be a crucial distribution channel for cyber threats and attacks like spear phishing. Impersonating well-known companies and sources in spoof emails is a growing trend. These can be used to spread malware, steal credentials, or carry out various types of online crimes and attacks.
One of the most effective protocols available today to combat email spoofing is DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC builds on earlier email authentication methods like SPF and DKIM to provide a multilayer defense against unauthorized use of domains in email. When implemented correctly, DMARC can stop spoofed emails in their tracks.
What is DMARC and How Does it Work?
DMARC is an email validation system that verifies the authenticity of the sending domain. The domain owner creates a DMARC DNS TXT record for their domain. This record tells receiving mail servers what to do if an incoming email fails validation – either reject, quarantine or monitor only.
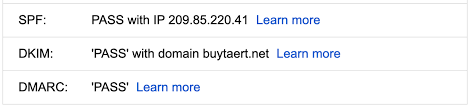
SPF and DKIM are used to authenticate the domain that sent an email. SPF checks that the sending IP address is authorized by the domain’s SPF record. DKIM checks that the email headers and body have not been modified in transit using a digital signature.
The DMARC TXT record includes several tags:
- v – Version of DMARC being used
- p -Requested handler policy (reject, quarantine, monitor)
- pct – Percentage of messages subjected to policy
- ruf – URI for aggregate feedback reports
- rua – URI for message-specific forensic reports
The DMARC policy published in a domain’s DNS tells receiving mail servers what to do if neither SPF nor DKIM authentication passes for an email claiming to be from that domain. For example, the policy could be “quarantine” or “reject”. DMARC analyzes the authentication results from SPF and DKIM, and If neither passes and the DMARC policy is “reject”, the email is rejected rather than delivered. This prevents spoofing of the domain.
DMARC Reporting for more email Visibility
One of DMARC’s key benefits is the full email authentication reporting it gives sender domains. This information provides anti-phishing defenses with previously unheard-of visibility into email spoofing attempts.
There are two main types of DMARC reports: Aggregate reports and Forensic reports
Aggregate DMARC Reports
An aggregate DMARC report, often prepared daily, weekly, or monthly, offers a thorough summary of email authentication results and actions done on messages based on the published DMARC policy over a specific period. The report includes a statistical overview, including the total number of messages examined, the quantity and percentage of messages that passed or failed DMARC alignment via SPF and DKIM, and a breakdown of the actions taken, such as rejections, quarantines, or rewrites. IP addresses, domain names, and geographic information are given in the source data for sources that fail authentication.
The report also provides granular data on the percentage of emails that passed DKIM only, SPF only, both, or neither, and the specific DKIM and SPF results. Recommendations are outlined for improving DMARC effectiveness based on the aggregated data. Raw XML data contains underlying record-level details not in the report summary which can be parsed programmatically. Reviewing the wealth of information in periodic aggregate reports is essential for monitoring the health of DMARC policies and fine-tuning protections against email threats.
Forensic DMARC reports
Forensic DMARC reports include comprehensive records on each email message that failed SPF or DKIM alignment for a particular domain, offering thorough information to aid in investigating and resolving DMARC authentication problems. These reports are generated by email receivers and providers for example, Gmail or Microsoft, and can be requested by adding a “ruf” tag to a domain’s DMARC DNS TXT record.
Forensic reports include the full message headers, source IP addresses, failure reason codes (e.g. SPF permerror), and snippets of email content to aid analysis. They help identify patterns in email spoofing attempts against a domain and pinpoint specific configuration problems leading to DMARC failures. Forensic reports are typically provided in a compressed CSV or XML data format and can encompass a high volume of records, requiring filtering to focus on suspicious traffic. While aggregate reports give a high-level view, forensic reports drill down into granular details on individual DMARC authentication failures to uncover email threats.
The forensic and aggregate reports offer priceless visibility at both a wide and detailed level. DMARC senders can track the results of authentication over time to find problems and abnormalities. When problems occur, they can be examined to locate and resolve the underlying reasons.
Why DMARC is Important for Email Security
DMARC is critical for email security for a few key reasons:
1. Prevents spoofing and phishing
Receivers can use DMARC to determine with certainty whether an email purporting to be from a specific domain is real or a forgery. This stops attackers from convincingly using protected domains to send phishing emails.
2. Drives adoption of authentication
Senders are encouraged to implement SPF and DKIM by DMARC policies correctly. There would be less motivation to implement these safeguards if DMARC did not reject unauthenticated messages.
3. Provides visibility
Unprecedented insight into domain-specific email spoofing is provided by DMARC reports. This makes it possible for security teams to monitor problems and improve defenses continuously.
4. Flexible policy controls
The diverse policy options provided by DMARC go beyond binary accept or reject. For instance, suspected fake mail could be quarantined or given extra analysis rather than being rejected outright.
5. Increased user trust
Customers are guaranteed the legitimacy of emails from protected domains by strict DMARC regulations. This increases user engagement and trust in verified brand communications.
6. Industry Momentum
Major email providers and industry groups endorse and encourage DMARC adoption. Momentum continues to grow thanks to demonstrated success in fighting phishing and spoofing.
With a combination of DMARC policies and advanced security gateways, organizations can shield users from phishing and fraudulent emails effectively. DMARC helps businesses to safeguard crucial communications, safeguard their brand, adhere to rules, and increase user confidence with the most thorough email authentication standard currently available.
To successfully resist email spoofing and fraud, companies should continuously review DMARC reports and gradually tighten regulations over time. Undoubtedly, threats will keep on changing, but careful DMARC adoption across industries can stop email communications from being used as a weapon against the public.
![]()