Email authentication is the process by which a sender is validated through published records, such as SPF, DKIM, and DMARC, that they are who they imply to be. With subject lines such as “Suspicious Account Activity,” “Invitation to Connect,” or “Urgent Wire Transfer Required,” phishing emails can trick people into divulging usernames, passwords, and other sensitive information to scammers. In addition, this harms the reputations of the businesses whose identities are spoofed.
These messages often include spoofed addresses and appear to include links to the businesses’ web sites, making it difficult to tell the difference between real messages and spoofed ones. The best way to prevent people from falling for phishing messages is to keep these scam emails from ever showing up in their inboxes. Validating emails helps organizations to take control of their sending domains and protect their brand reputation. Using SPF, DKIM, and DMARC, businesses can determine who is authorized to send emails on behalf of their domain.
Email authentication is critical as email addresses are easy to forge
Altering an email address and making it appear as a trusted source to the receiver is something you and I can do. It does not require any technical or black hat expertise. How come? This is because the basic protocol that makes sending and receiving emails between computers easier only requires that the email address in the ‘To’ line be valid. All other information can be inaccurate. This protocol is known as the Simple Mail Transfer Protocol.

Scammers take advantage of this design by altering the “From” address. With emails, there are two types of ‘From’ information, that is, the ‘envelope from’ and the ‘header from’. The ‘Envelope From’ indicates which server the email originated from. It is the return address that tells mail servers where to return, or bounce, the message back to. It’s contained in the hidden email message header, which includes other technical details servers use to understand who the message is for, what software was used to compose it, etc.
On the other hand, the ‘Header From’ is the information a user will see on the ‘From:’ line of an email. With SMTP, these two types of ‘From’ information don’t have to match and can both be inaccurate. It is quite easy for cybercriminals to forge this information and send out large numbers of phish emails.
This is why businesses require additional authentication protocols in their anti-phishing emails. These protocols supplement SMTP to provide the best protection against phishing emails.
How does email authentication stop phishing and spoofed emails?

Email authentication involves three protocols that work together to stop spoofing which is used to create phish emails. They help to:
- Provide insights about emails that failed authentication which helps your IT department to monitor and observe spoofing efforts.
- Identify legitimate emails that end up in junk folders falsely after being marked as unauthenticated.
- Verify the sender and contents of an email
- Control what happens to unauthenticated emails
These three important email authentication protocols are;
- SPF (Sender Policy Framework)
- (DKIM) DomainKeys Identified Mail
- DMARC (Domain-based Message Authentication Reporting and Conformance) authentication
1. Sender Policy Framework (SPF) Authentication
SPF helps organizations declare which email servers or hosts can send emails from their domain. It also provides a way for the receiving organization to check for this authentication and accept the email. Thus, SPF also ensures that an email reaches the intended mailbox.
With SPF authentication, your organization verifies and authorizes hosts or mail servers and networks to use its domain names when sending emails. Additionally, it also provides a way that a receiving host (server) can check that authorization. In other words, when you create an SPF record, it lists which email servers are allowed to send emails from that domain. Therefore, this system helps to prevent spoofing of sender email addresses by alerting your organization that the domain it claims to be from has not authorized the IP address to send emails on behalf of that domain.
How SPF authentication works
SPF is an email authentication protocol that allows the owner of a domain to specify which mail servers they use to send mail from that domain.
Brands sending emails publish SPF records in the Domain Name System (DNS). These records list which IP addresses are authorized to send emails on behalf of their domains.
During an SPF check, email providers verify the SPF records by looking up the domain name listed in the “envelope from” address in the Domain Name System (DNS). The domain name system (DNS) is a naming database where internet domain names are located and translated into IP addresses. If the IP address sending email on behalf of the “envelope from” domain isn’t listed in that SPF record, the message fails SPF authentication.
Step by step SPF authentication
1. Creating the SPF record; Your domain administrator creates an SPF record that lists all the mail IP addresses allowed to send emails from the domain mailsafi.com.
2. Implementing the SPF record; Your domain, mailsafi.com, which is the sending domain adds the SPF records to its DNS.
3. Verifying the SPF record; During an SPF check, your email service provider verifies the SPF record by looking up the domain name listed in the “envelope from” address in the DNS. If the IP address sending email on behalf of the “envelope from” domain isn’t listed in that SPF record, the message fails SPF authentication.
SPF authentication is not foolproof
As effective as SPF authentication is, it has its shortcomings. They are;
- Updating SPF records is difficult due to a lack of visibility. For example when businesses change service providers or add new mail streams
- When a message fails SPF, this does not mean it is always blocked from reaching your inbox. SPF is just one of several factors email providers take into account.
- SPF verifies incoming emails except when a user forwards the message or uses automated forwarding
- It does nothing to protect brands against cybercriminals who spoof the display name or “header from” address in their message. It is the more frequently spoofed “from” address since it’s the address most visible to the email recipient.
In conclusion, SPF authentication not only allows an organization to authorize hosts (servers) and networks to use its domain names when sending emails but also provides a way that a receiving host can check that authorization. However, SPF is not a stand-alone defense system against phishing.
2. DomainKey Identified Mail (DKIM) Authentication
This is the second protocol in the email authentication process. DKIM provides a digital signature that claims responsibility for an email also known as the DKIM signature. A DKIM signature is a header added to email messages. The header contains values that allow a receiving mail server to validate the email message by looking up a sender’s DKIM key and using it to verify the encrypted signature.
In addition, it guarantees an email has not been altered. Therefore, it allows an organization to take responsibility for transmitting a message in a way that can be verified by your email provider.
How DKIM email authentication occurs
As mentioned, to use DKIM, email servers attach special DKIM signatures to the emails they send. These signatures travel with the emails and are verified along the way by the email servers that move the emails toward their final destination. These signatures act as a watermark for email so that email receivers can verify that the email actually came from the domain it says it does and that it hasn’t been tampered with.
Each signature contains all the information needed for an email server to verify that the signature is real, and it is encrypted by a pair of keys. The originating email server has what is called the “private key,” which can be verified by the receiving mail server or ISP with the other half of the key pair, which is called the “public key.”
Step by step process of DKIM authentication
The process begins by deciding what elements of an email to assign the DKIM signature. This can be the entire message or specific fields of the email header. Whichever the case, the elements chosen for the DKIM signing process must remain the same during transit in order to pass DKIM signature authentication
After choosing which elements to include in the signing process, the sender configures their email platform to automatically create a hash of these elements
The encryption process
Cryptography is at the center of the encryption process. Before sending the email, a private key encrypts the hash string. The private key is then assigned to a unique combination of domain and selector. The DKIM selector is specified in the DKIM-Signature header and indicates where the public key portion of the DKIM key pair exists in DNS. The receiving server uses the DKIM selector to locate and retrieve the public key to verify that the email message is authentic and unaltered.
Authenticating the DKIM signature
A public key authenticates the DKIM signature. To validate the signature, the mailbox provider will run a DNS query to find the public key for that domain/selector combination. This public key is unique and is the only match for the private key that signed the email, also known as a keypair match we mentioned earlier. The keypair match enables the email provider to decrypt the DKIM signature back to the original hash string.
The message recipient then takes the elements of the email signed by DKIM and generates its own hash of these elements.
Finally, the recipient compares the hash it generated with the decrypted hash from the DKIM signature. If they match, we know that the sender truly owns the email and that the signed elements remain unchanged during transit.
3. Domain-based Message Authentication Reporting and Conformance (DMARC)
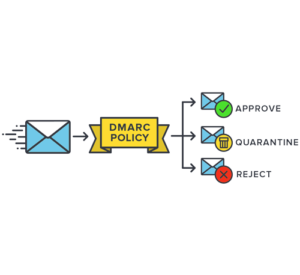
DMARC is all about verifying that the email address in the “From” header actually comes from the actual sender. This is how DMARC completes a comprehensive anti-phishing defense system as neither SPF nor DKIM can prevent spoofing of the header “From”.
DMARC ensures email is properly authenticating against established DKIM and SPF standards. It ensures that fraudulent emails appearing to come from domains under your organization’s control are blocked. Two main aspects of DMARC makes this process. That is, domain alignment and reporting.
SPF and DKIM alignment is DMARC authentication
This process involves;
- Matching the “header from” domain name with the “envelope from” domain name used during an SPF check
- Matching the “header from” domain name with the “d= domain name” in the DKIM signature.
To pass DMARC, an email must pass SPF authentication and SPF alignment and/or DKIM authentication and DKIM alignment. A message will fail DMARC if the message fails both (1) SPF or SPF alignment and (2) DKIM or DKIM alignment.
Moreover, DMARC allows senders to instruct email providers on how to handle unauthenticated mail using a DMARC policy. This eliminates any guesswork on how they should handle messages that fail DMARC authentication. Senders can either:
- Block delivery of unauthenticated messages (noted in the DMARC listing as “p=reject”),
- Quarantine or place unauthenticated messages in the recipient’s junk email folder (noted in the DMARC listing as “p=quarantine”), or
- Give no specific guidance on how to treat unauthenticated messages (noted in the DMARC listing as “p=none”).
Additionally, we mentioned that email authentication provides useful insights into spoofing efforts. Organizations can use the “p=none” instruction in conjunction with a request for receiving domains to send it reports about authentication failures. This enables the sending domain to monitor whether its SPF and DKIM DNS entries are working properly.
To conclude, DMARC is the latest and only widely deployed technology that can verify the “header from” address (what users see in their emails). Not only does this help protect customers and the brand, it discourages cybercriminals who are less likely to go after a brand with a DMARC record
The Takeaway
- Firstly, email authentication prevents the entry of spoofed and phish emails into your mailbox
- An SPF record determines which email servers are authorized in sending emails on behalf of your domain
- A DKIM record confirms that the message is unaltered
- Creating a DMARC record prevents spoofing of the header “from” email address which is the display name that users see
- Implementing DMARC policy instructs your domain’s receiving servers on what to do with emails that fail authentication
- A DMARC policy can either quarantine, reject, or do nothing to unauthenticated emails
- To implement a full-proof anti-phishing solution, you need the full capacity of all three email authentication methods
Conclusion
Email authentication technology is affordable and available to businesses of all sizes. With third-party email service providers, implementing email authentication solutions can be complex. This is because changes made on these systems affect your business. To solve this challenge, it is advisable to ask your provider to set no specific guidance on how unauthenticated emails are treated at first.
Monitor and observe how the systems work while noting if there are any legit emails failing authentication. Depending on what business your domain engages in and its popularity, you can adjust your DMARC listings accordingly with time.
Finally, it is important to note that email authentication is crucial for a Software as a Service (SaaS) company. This is because it confirms that your users receive emails truly sent from your product. Implementing all three forms of authentication is the best way to protect your application’s reputation.
MailSafi protects your mailbox and network with SPF, DKIM, and DMARC authentication. Implementing these protocols can be complex. Contact us to learn more about MailSafi Email Security mail validation technology.
![]()



Pingback: What is Blacklisting? » The MailSafi Blog
Pingback: 15 Must-Have Features For Your Spam Filtering Service » The MailSafi Blog
Pingback: What is DMARC and How Does it Work » The MailSafi Blog