1. What is Two-factor Authentication?
Two-factor authentication (2FA) – also known as two-step verification or dual-factor authentication or multifactor authentication (MFA) – is a method of establishing access to online accounts (including email accounts) that requires a user to provide two different types of information.
For business, two-factor authentication is useful when accessing email via a web interface.
A factor in this context means a way to prove to a system that you are who say you are so that the system can determine if you are authorized to access the account that you’re trying to access.
When it comes to email, the most common authentication factor in use today is the username/password pair. With two-factor authentication, you’ll need to both provide a password and prove your identity some other way to gain access.
As passwords have become increasingly less secure, either because of data breaches or poor email security practices, many more business email users are moving to 2FA to secure their data. Many service providers encourage or mandate the shift as well.
Scenario 1
You may not realize it, but you use two-factor authentication more often than you think. When you go to the supermarket checkout, swipe your debit card, and key in your PIN code, this is an example of two-factor authentication. You first produce the debit card, and second, you have to know your PIN code.
Scenario 2
Another example is when you go to the bank counter to withdraw cash from your bank account. The bank may require you to either;
- Write a check (which you sign), or,
- Complete and sign a cash withdrawal request (which you also sign).
The bank will then ask you to show proof of your identity. Proof of identity may be in the form of your national identity card, passport, or other form of identity which has your passport photo (mugshot). In this case, your signature is the first factor, while your identity card is the second factor.
Essentially, two-factor authentication requires two ways of proving your identity. This concept can then also be applied to protect your email accounts.
2. Understanding the types of authentication
There are three types of authentication:
- Something you know – for instance, a password, PIN code, or answer to a security question (for example, mother’s maiden name, favorite pet, and so on).
- x Something you have: identity card, driver’s license, debit or credit card, a phone, or fob.
- Something you are: biometrics (fingerprint, retina scan, face scan, or voice recognition).
Some systems also allow you to restrict access to email accounts by location. Setting restrictions by location means limiting authentication attempts to a specific device in a particular place (IP or GPS data).
You may also use time as an authentication factor. A time factor restricts authentication to a specific time window. Outside that timeframe, it is not possible to log in.
Location and time are useful for restricting access. However, we will limit our discussion to the first three types of authentication discussed above as the vast majority of 2FA methods rely on these. Systems requiring greater security can apply time or location as a factor to implement multifactor authentication (MFA).
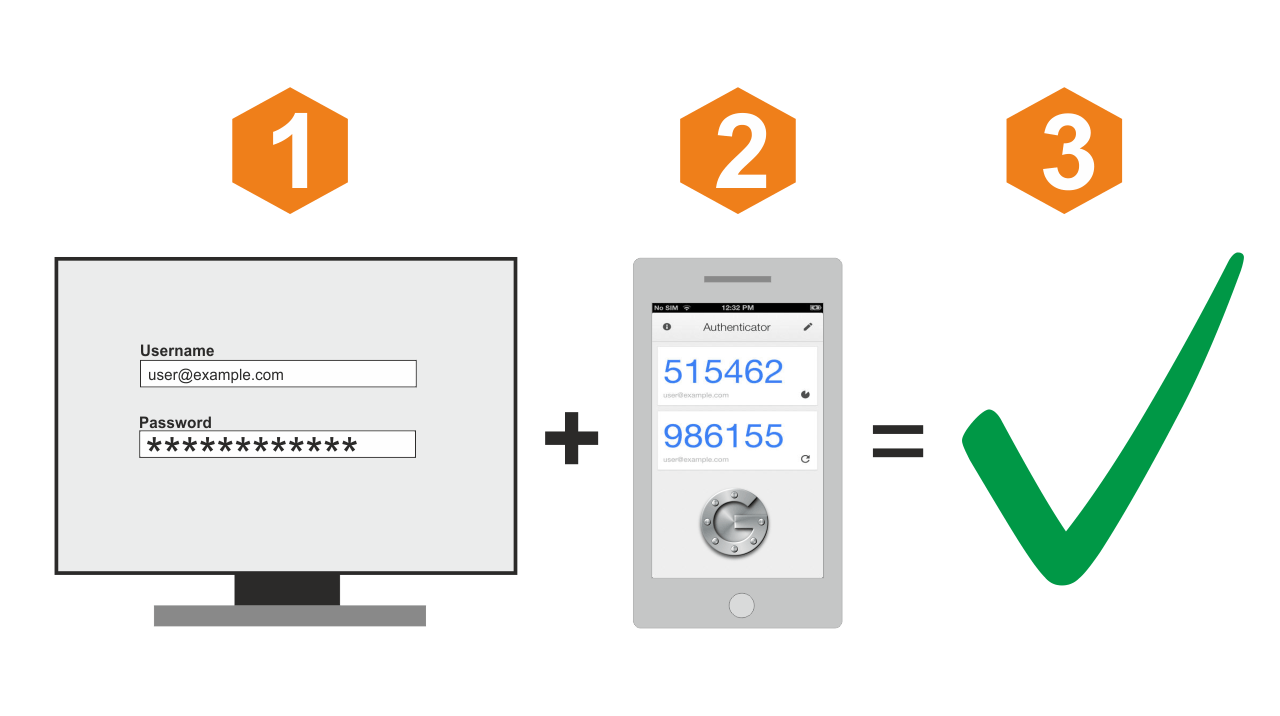
3. How does two-factor authentication work?
When it comes to email access, you’ll need to enter your username/password – the first authentication factor. Next, you will have to either;
- Wait for a code – the second factor – to arrive via text message (SMS) on your phone. That is, you’ll get a text with a numeric code that you then need to enter to access your email account.
Unlike the PIN code for a debit card, a 2FA code is only valid for one-time use. It expires after a specified duration. Each time you log into your email, you will receive a new code.
2. The second option is when you log in with a username/password, you are asked for an authentication code – the second factor. Then you go to your phone, open your authentication app, and then key in the active code displayed on the screen. This code will expire after a few seconds, and a new code will be automatically generated. Popular authentication apps are Google Authenticator, Authy, and DuoMobile.
This second step means a hacker needs to steal both your username/password and your phone to access your account.
Many service providers encourage their users to activate 2FA to protect their users’ credentials from being used by hackers who have stolen a password database or used phishing to obtain user passwords.
MailSafi offers 2FA via Google Authenticator. If you haven’t already, please read more about why using SMS (text message) for 2FA isn’t such a great idea – here.
4. Why isn’t Single-Factor Authentication (SFA) enough?
Passwords have remained the most common form of SFA because of their low cost, ease of implementation, and familiarity. However, by their nature, passwords are limited when it comes to security for the following reasons:-
- It requires knowledge and diligence to create and remember strong passwords.
- Passwords require protection from many inside threats like carelessly stored sticky notes with login credentials, old hard drives, and social engineering exploits.
- Passwords are prone to external threats, such as hackers using brute-force, dictionary, or rainbow table attacks.
Even enough time and resources, a hacker can usually breach many password-based security systems and steal corporate data.
5. Why is 2FA important for my business email?
The username/password pair has been the standard for everyday email access for generations now. Why now bother to make logging into your account more difficult?
Well, over the years, widespread major data hacks have made it possible to put up millions of email usernames/password pairs up for sale on the dark web making many passwords less secure. Additionally, most people reuse passwords across multiple sites and accounts; a hacker can plug in known email address/password pairs into dozens of sites and see which of them provides access. Verizon’s 2017 Data Breach Investigations Report
found that 81% of account breaches could be put down to passwords that were either leaked in this way or passwords that were so weak (e.g., “passw0rd”) that they were trivially easy to guess.
Two-factor authentication adds an extra layer of security to the authentication process by making it harder for hackers to access a person’s account because knowing the user’s password alone is not enough to pass the authentication check.
Therefore, it is crucial to add a second layer of security – and the second layer must be something you have or something you are. It is not wise to combine two similar factors, i.e., something you know (like username/password + your mother’s maiden name). These are both knowledge-based authentication and do not represent true 2FA. You’re just backing up something you know with something else you know. In essence, the answer to your security question is just another password and subject to all the same weaknesses. Both can be guessed or social engineered.
6. Isn’t 2FA Cumbersome? Will it make my email more secure?
2FA may be considered by some as cumbersome. However, we must agree that the small hassle of a second step of authentication pales compared to the stress of getting hacked.
That said, it is important to understand that no security feature (for email or your house or otherwise) can claim to offer 100% foolproof protection. However, by combining two of the above three authentication types, you minimize the risk that a hacker will access your email account and gain access to confidential corporate data.
You not only make your email accounts more difficult to attack, but you also make your accounts less attractive targets.
Scenario
Think of it in terms of home protection. If you have an electric fence, you lower the odds of a burglary. Also, if you have burglarproof doors/windows, you lower the odds of a burglary. If you have a loud, large dog, you also reduce the odds of a burglary.
However, if you combine burglarproof doors/windows with a big dog, or burglarproof doors/windows with an electric fence, your house becomes even more challenging to break into and, therefore, a less attractive target. Most burglars will find an easier mark – one without burglarproof doors/windows, an electric fence, or a menacing dog.
Likewise, two-factor authentication prevents a large portion of hackers from targeting your account; many hackers will move on and find easier accounts to compromise. Should they still choose to target you, they’ll need more than just your username/password. In addition to your password, a hacker needs to have your phone also or access the tokens placed on your phone by the authentication mechanism via a phishing attack, malware, or activating account recovery. By activating account recovery, your password is reset, and 2FA is disabled. That’s a ton of extra work.
7. Conclusion
Two-factor authentication provides a higher level of security than authentication methods that depend on single-factor authentication (SFA) in which the user provides only one factor – typically, a password.
Although 2FA requires an extra step when logging into your email, it is a small price to pay (a few seconds to be precise) to minimize your email’s risk of being compromised or hacked. Your email will undoubtedly be more secure with 2FA. Email security is especially crucial for businesses because their email most often have confidential information relating to the company or its clients.
MailSafi’s cloud-based email solution for business supports two-factor-authentication (2FA). It will allow your users to tighten security when they are accessing their emails via webmail. MailSafi also supports app-specific passwords for added security on mail clients such as Outlook, Thunderbird, and so on. Contact us today for more information.
![]()




Pingback: SMS for 2FA (Two-factor authentication: Why it's not a Good Idea | MailSafi
Pingback: Application-specific passwords explained | MailSafi
Pingback: Compromised email or hacked email account: How to fix it | MailSafi
Pingback: The Role of Employees in Your Fight Against Spam
Pingback: Business Email Compromise: Understanding and Preventing | MailSafi
Pingback: Cybersecurity Awareness Training Topics for 2021 | MailSafi
Pingback: Egregor Ransomware Attack Warning from FBI | MailSafi
Pingback: You don’t need to change your password regularly or frequently | MailSafi
Pingback: How SIM-SWAP Fraud Affects Your SMS-based 2-FA | MailSafi
Pingback: 6 Risks of Public WiFi and How to Stay Safe
Pingback: Protect Your Hotel From Cybersecurity Threats: 13 Steps | Kaluari
Pingback: The Russia Ukraine Conflict - Cybersecurity Threats | Kaluari
Pingback: 6 Reasons not to use Free Web-Based Email for Your Business
Pingback: An Easy 9 step Checklist to assess your email security.
Pingback: Choosing the Right Email Service Provider: 12 Factors to Consider » The MailSafi Blog