Public WiFi can pose a significant threat for businesses or individuals using them for work.
It is not uncommon to walk into many coffee shops on a weekday and spot a large number of customers working on their laptops. Today, many entrepreneurs, students and businessmen and women treat these locations like a second office. WiFi in most of these places is usually free, but not always, for patrons.
The same applies to WiFi in hotels, restaurants, airports, bookstores, libraries and some retail outlets. Effectively, you’re never too far off from a public WiFi hotspot to access the internet and your work email or documents for those with access to team collaboration tools. Most guests, especially those on business meetings or on holiday and therefore sleeping over at the facility, will often access the free WiFi offered in these spaces.
A large number of people who access public WiFi often access sensitive or confidential company or personal information on their devices. Unfortunately, many of these users are unaware of the threat posed by accessing the internet over public WiFi.
In this article, we discuss:
- The risks of using public.
- 8 tips on how to stay safe when accessing WiFi in public areas using public WiFi.
1. The Risks of Using Public WiFi
It is important to understand the risks of using public WiFi to keep you situation-aware. A study carried out by the Kaspersky Security Network showed that nearly a quarter of the world’s public WiFi hotspots do not use any kind of encryption. It is critical to ensure that the WiFi network you are connecting to is encrypted. Nevertheless, there are still other threats posed in the use of public WiFi even if a hotspot uses encryption.

i. Theft of the Data Held Your Device
One of the most serious and typical threats of accessing public WiFi is the theft of personal information. Personal information includes:
- Login credentials (username, password, passcodes)
- Financial information (credit or debit card details)
- Personal data (full names, photos, Identity card or social security number)
If a cyber-attacker gets access to your laptop or other smart devices through an insecure public WiFi connection, the hacker can have access to all the data held in the device and even beyond. For example, they can:
- Use your credit card or debit card details to transact online
- Note your email login credentials to impersonate you with the aim of committing fraud
- Use your personal data (full names, identity numbers, photos) to perpetrate fraud such as creating new accounts, perpetrating SIM-SWAP fraud
ii. Man-In-The-Middle Attacks (Impersonation Attacks)
Even where a cybercriminal fails to gain access to the data on your device, they can still intercept the information you are sending over the internet. This is how they can capture usernames and passwords, credit card details, and other confidential information.
You can think of a man-in-the-middle attack simply as eavesdropping. Two parties may be connecting to each other (via email, video calls, browsing, etc) but a third party intercepts their communication/connection.
Where public WiFi is concerned, this is typically how a man-in-the-middle attack works.
Step 1 – The Deceit
You may be accessing WiFi at a coffee shop or hotel. The facility gives you the WiFi network name and password. You settle in and select the WiFi network – without paying close attention to the network name. There may be two with similar names, e.g., CafeR and CaffeR. While CafeR may be the legitimate connection, you may select CaffeR without giving it much thought. You log in and start working.
Step 2 – The Data/Credential Capture
What you didn’t know is that CaffeR has in fact been set up by a hacker who’s sitting not too far away from where you are. The hacker has set up a hotspot with a name similar to that of the facility to trick you and other unsuspecting patrons.
When you connect to CaffeR, everything appears to work as it should, and therefore there is no cause for alarm. However, in reality, what is happening is that everything you’re doing on that internet connection is being tracked on the hacker’s device. The hacker in this case is the man-in-the-middle. He or she can easily capture your login credentials and everything else you do on that “public WiFi” connection.
Step 3 – The Impersonation Attacks
Armed with this information, the “man-in-the-middle” can then proceed to use information captured for further attacks. For instance, they may:
- Use any confidential personal or client data captured to demand ransom from you
- Access your email to impersonate you with an aim of committing Business Email Compromise/CEO Fraud Attacks
- Login to your business email account to send malicious files (malware, viruses, spam) or links to people you know
- Access your bank accounts and transact
- Use your credit card details for online purchases
It takes longer to detect an impersonation attack. Oftentimes, the damage has already been done, resulting in a financial or reputational loss.
Fun fact: Common abbreviations for a man-in-the-middle attack include MITM, MitM, MiM, and MIM.
iii. Unencrypted Connections – Packet Sniffing/Eavesdropping
When you connect to a website that supports encryption, the data that goes back and forth is encoded using a secure key. If anyone was to intercept that data without the possession of the secure key, they would not be able to read it. The data would appear unreadable like computer code. This is in fact the ideal setup.
Unfortunately, not all websites offer encryption. If you have come across a website address prefixed with just HTTP, this is a sure way to know it is not encrypted. If it starts with HTTPS, then the website is encrypted.
When you are connected to a public WiFi network, anyone within range of your device can intercept everything you send or receive.
Therefore, if you access an unencrypted website, it will all be fully readable by the other party who has intercepted your connection. To eavesdrop on your connection, a hacker will use a tool called a packet analyzer or packet sniffer. Packet analyzers or packet sniffers allow viewing of everything transmitted over the unencrypted connection
Note: Packet sniffers and packet analyzers are not bad tools. They, in fact, have positive use cases. For instance, network administrators can use them to troubleshoot network connection problems with their wireless networks.
iv. Distribution of Malware
Another risk of using Public WiFi is that a cyber attacker can install malware on your device. Malware includes:
- Viruses
- Worms
- Trojan horses
- Ransomware
- Adware
A malicious actor on the same public WiFi as you can install malware on your device if it is not properly secured. Such malware may cause your device to malfunction or steal data from it.
A malicious WiFi service provider may also use the opportunity to overlay every website you visit with ads. In this case, the ads would normally disappear as soon as you disconnect from the free WiFi.
v. Your Session Can be Hijacked
Session takeover is another public WiFi security threat. In this case, an attacker intercepts information about your computer and its connection to websites or other services. Once the attacker has that information, he can configure his own computer to match yours and hijack the connection.
For instance, a hacker can hijack your connection to your bank’s online portal after you log in. From the bank’s end of the connection, it appears as though this is still your device, and since you are already logged in, the cyber attacker would have access to all your bank details on the portal.
vi. Your Data May Be Captured and Sold to Advertisers
You may be working remotely such as when on a road trip, away on holiday or even stuck in traffic. You may find yourself connecting to public WiFi to check your email, view or download files, review clients’ details and so on.
As earlier mentioned, many of these public WiFi services are often offered free of charge. However, as you’ve probably already come to realize that “free” is not always free. There must be some benefit derived by the service provider to offer this for free. In this case, some WiFi service providers may be tracking everything you’re doing on the WiFi connection and sell your data to advertisers for a fee.
3. How to Protect Yourself From the Risks of Public WiFi
Learning how to protect yourself when accessing the internet and other internet resources in public spaces will go a long way in ensuring your business and personal data remains safe.
If you must use public WiFi, here are some tips on how to protect yourself from the threats discussed above. While some are more effective than others, keep in mind that hackers tend to aim for the path of least resistance. If you have taken some steps to protect yourself, they will more likely abandon their attempt to attack you and move on to an easier target.
i. Use Cellular Data or a Mobile Hotspot in public spaces
The safest way to avoid the threats of public WiFi is to simply avoid it. Even if you must browse in that café, on holiday, etc., consider investing a little more to ensure you’re browsing on a secure network. Consider using your smartphone or tablet for example, as a mobile WiFi hotspot – using your known cellular data – from your trusted service provider’s network. Today, some of the latest smartphones and tablets support digital eSIM There is growing adoption of eSIMs as well as mobile hotspots for international travelers as they make it less cumbersome for people who travel across borders to set up mobile hotspots without having to constantly acquire new SIM cards in every country. Mobile hotspots can also be shared between multiple devices and therefore shared between different users working away from the office.
Using your own private connection is not only more secure than a public WiFi connection. It is also faster as it’s not being shared with multiple users at the facility you’re at.
However, we understand that sometimes you have no alternatives and may need to access public WiFi – such as stuck in a new country or in transit in an airport or simply run out of funds to pay for your cellular data! As mentioned earlier, most hackers will look for easy targets. Here are a few precautions you can take when you must access public WiFi.
ii. Don’t Access Sensitive Sites or Email
First, if you must connect to a public WiFi network with no protection measurements in place, make sure not to share anything private or log into any sensitive websites. This includes:
- Online shopping checkout (which would require you to key in your payment details)
- Internet banking
- Accessing medical or insurance (health, life) records
- Checking office
iii. Keep your browsing to a minimum
Disconnect from public WiFi as soon as you find the information you need.
iv. Use a Virtual Private Network (VPN) Service
Where possible, use a virtual private network (VPN) when connecting to your business through a suspect connection like a public WiFi hotspot. With a virtual private network (VPN) service, everything you send and receive over a WiFi network is encrypted, regardless of whether the WiFi network or website you are accessing supports encryption.
With a VPN, you connect to the VPN server over an encrypted connection and everything you do gets routed through that server. This means that anyone trying to eavesdrop or intercept your data will not be able to read it anyway. Since most hackers are after an easy target, they’ll most likely discard any stolen data that is encrypted rather than going through the lengthy process of trying to decrypt it.
v. Use SSL
You may not have access to a VPN for general internet browsing. However, if you enable the “Always Use HTTPS” option on websites that require some kind of authentication (username and password), this will add an extra layer of protection. Most websites that need the user to log in support SSL.
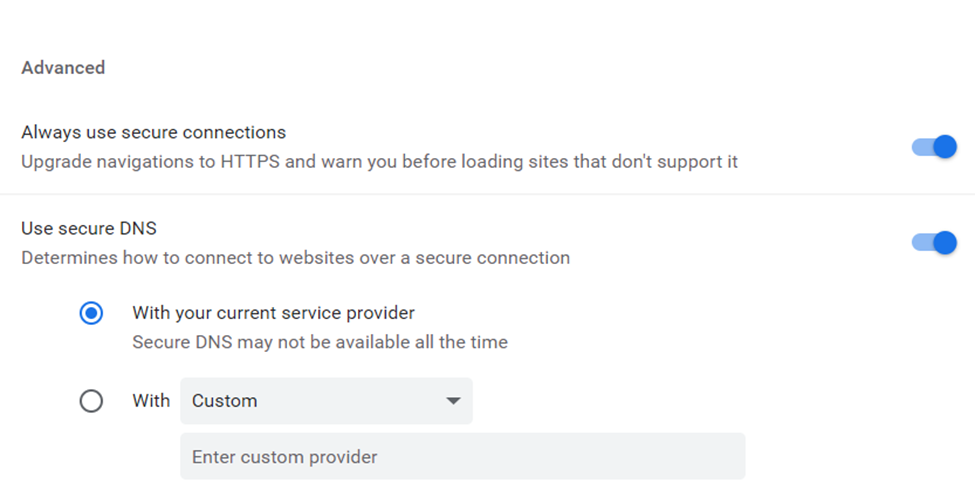
vi. Use Two-factor Authentication (2FA)
Activate two-factor authentication wherever possible – especially for sensitive services such as your business email, online banking, and websites where purchases are done. Two-factor or multi-factor authentication adds an extra layer of security to your account beyond the password. This may be a security code sent to your smartphone via a specialized app such as Google Authenticator. It may also be a biometric mode of authentication such as fingerprint scanning, retina scanning, face recognition. It can also be through a physical device such as a key fob. If a hacker manages to capture your login credentials such as username and password, they will still not be able to access your account without providing this second mode of authentication. Read more on the benefits of two-factor authentication and why you should use it
Read also why we do not recommend text messaging (SMS) for two-factor or multi-factor authentication and how SIM-SWAP fraud affects your SMS-based 2FA.
vii. Turn Wi-Fi off When You Aren’t Using It
Even if you haven’t actively connected to a network, the Wi-Fi hardware on your laptop or device is still transmitting data between any WiFi network within range. There are security measures in place that may minimize the risk of this minor communication causing a compromise. However, it may not work on all wireless routers, and some hackers can also find a way around it. Therefore, we recommend that if you only need to work on, say, a Word or Excel document, keep your Wi-Fi turned off.
As a bonus, your laptop or battery life will also last longer.
viii. Use endpoint protection on your devices
Where possible, use endpoint protection (antivirus, antimalware, firewalls) on all your machines and devices. These can help to automatically scan files downloaded on your machine.
Even individuals who take all the possible public Wi-Fi security precautions are going to run across issues from time to time. It’s just a fact of life in this interconnected age.
Get in touch with Kaluari for best-in-class gateway and endpoint security solutions. We partner with providers including but not limited to BitDefender, Sophos, Kaspersky and Barracuda Networks to offer security solutions tailored for your business environment.
We also offer advanced email security (spam filtering) services for businesses including email security for Microsoft 365. Our solutions are compatible with Exchange, Zimbra, MDaemon, shared hosting Cpanel, Linux MTAs, Office 365 and all other email platforms.
Our MailSafi email and collaboration service comes with our full suite of MailSafi Email Security for advanced protection.
4. Summary
Public WiFi can pose a significant threat to businesses and individuals using them for work.
However, throughout any business traveler’s life, a time comes when an unsecured, free, public Wi-Fi hotspot is the only option you have to get your urgent work done. Additionally, we also understand that the convenience of connecting to a free public WiFi can also be tempting and difficult to pass on. Understanding public Wi-Fi risks will ensure your important business data stays secure. Therefore, if you must use public WiFi, be alert and take measures to minimize the risk of theft of your data and personal information on public WiFi connections.
![]()




Pingback: Hotel Cybersecurity: Threats You Must Know | Kaluari