If you or your staff access protected information with authentication codes sent to your mobile phone, you might want to rethink this. Two-factor authentication (2FA) or multi-factor authentication (MFA) is not a problem. On the contrary. We highly recommend that you use two-factor (2FA) or multi-factor (MFA) authentication wherever possible. SMS-based two-factor or multi-factor authentication can, however, fall prey to SIM-SWAP fraud scams.
Overview
In this article, we will discuss:
- What is SIM-SWAP Fraud?
- How does SIM-SWAP fraud occur?
- What are the dangers of SIM-SWAP fraud?
- What are the risks of SIM-SWAP fraud when it comes to 2FA (two-factor authentication)?
- How can you avoid becoming a victim of SIM-SWAP fraud?
- What to do if you become a victim of a SIM SWAP scam
What is SIM-SWAP fraud?
So you’ve lost your phone, damaged your phone or you just need a new SIM card because your current one does not fit in your new phone. You walk into your nearest mobile service provider store and request a SIM-SWAP. There, done. Now I’m good to go! Or are you, really?
SIM-SWAP, once considered a fairly safe procedure, has in fact turned out to be a present-day scam across the globe resulting in heavy financial loss to multiple victims. In 2019, South Africa reported that SIM-SWAP scams had doubled in a span of a year. SIM-SWAP scams were also reported in UAE, Turkey and other parts of Africa.
SIM-SWAP is a form of identity theft. It occurs when fraudsters replace your SIM card so as to take over your line.
SIM-SWAP fraud occurs when fraudsters replace a customer’s mobile phone line and take over a customer’s line. The criminal fraudulently obtains a new SIM card from a mobile service provider using the victim’s registered phone number. This sometimes even happens with the assistance of the telco companies’ internal staff – working together with fraudsters. Fraudsters can even register an existing number on a new SIM card.
The end goal of SIM-SWAP fraud is to intercept notifications, messages, one-time passwords, online banking codes and profiles and transactions as well as changing account settings.
How SIM-SWAP Fraud is Done
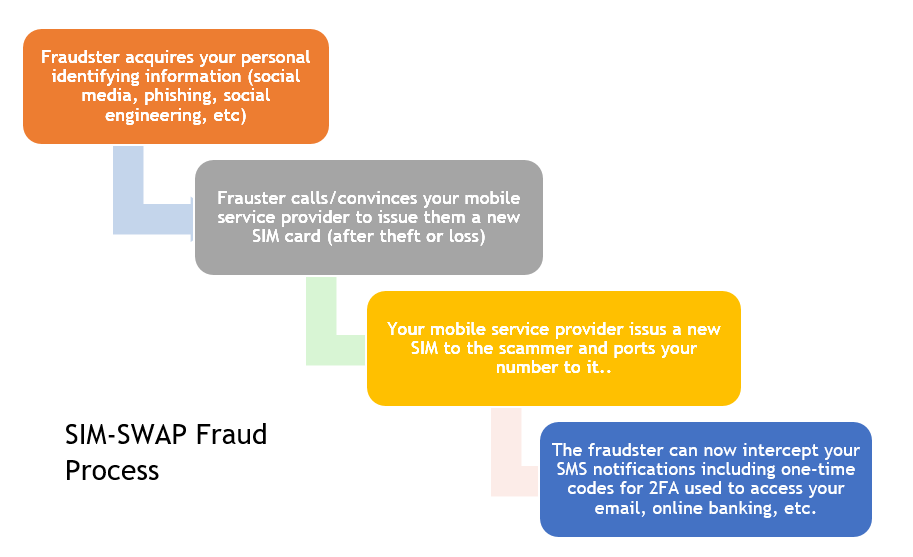
Stage 1
- The scammer will gather personal information about you.
- The fraudster will call you and identify himself/herself as being from your network service provider. He/she will refer to you by name, typically, your full name, and also read out your ID number to you to ask for confirmation of whether the digits are correct. This is a social engineering method used to get you to win their confidence.
Stage 2
- The fraudster will get you to follow certain instructions, typically, to dial certain codes on your phone. For example, USSD code 33*0000* or #253257# or ##72786#. These codes are intended to signal that you’ve lost your SIM card and are, therefore, initiating the process of a SIM-SWAP.
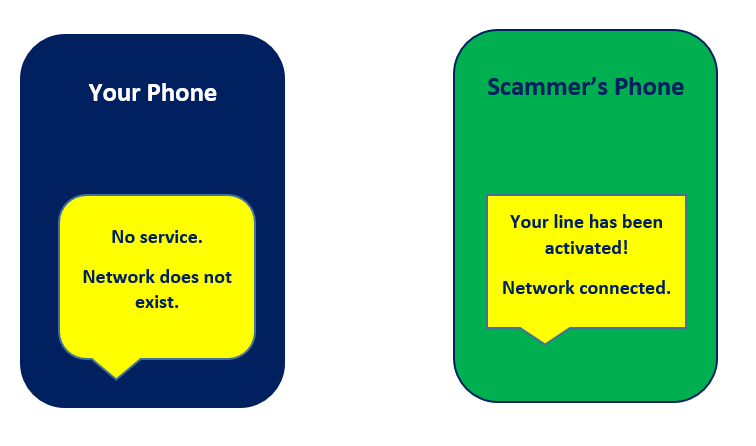
- Once you initiate this process, the network on your device/handset disappears. While you’re offline and struggling to figure out why and probably getting in touch with your network service provider or heading to their shop, the fraudster contacts your network service provider impersonating themselves as you. They’ll report their phone and/or SIM as stolen and ask for replacement.
- The fraudster will, thereafter, provide your details to the mobile service agent who will unknowingly help in issuing a new SIM and reactivating the line. You may receive a message on your SIM saying “Your SIM-SWAP application was successful.” However, you will no longer be able to access your text, mobile money, make calls, access the internet or perform any other tasks on which relied on the SIM to function.
- The fraudster will now have access to all your SIM services including calls, text messages, mobile money, mobile banking, etc.
Other ways in which this can happen include a stranger having a convincing story that allows him to simply have the phone owner willingly hand over his phone handset to him. For instance, the fraudster may request to make a call on your phone because he has lost his phone, or pretend to be a mobile money agent who wants to sort out an issue with your phone. Even so, quite a number of these scams involve compromised staff working with the mobile service provider.
Summary of Dangers of SIM-SWAP
Having your SIM swapped by a fraudster who takes over your phone is not just an inconvenience. Once a criminal takes over your phone number, they can use it to:
- Impersonate you and/or log into your online accounts.
- Get instant access to any two-factor authentication codes you receive through text messages, the secret code that a company or service provider would ordinarily text you to verify your identity.
In effect, if the scammer has your password or other personal identifying information, they’re just a few clicks away from accessing your email account, bank account and/or social media accounts. Anyone with access to your email account can:
- Scour through your email archive to build a list of your entire online presence.
- Change your other account passwords, effectively locking you out of your accounts.
- Log in to your bank account and steal your money or take over you.
How to Avoid Becoming a Victim of SIM-SWAP Fraud
Here are a few ways to avoid becoming a victim of SIM-SWAP fraud.
DO NOT:
- Don’t reply to calls, text messages or emails that request for your personal information: Should you receive a call from a stranger (even who introduces him/herself as being from your phone company), do not follow instructions to key in anything on your phone. Instead, contact the company directly using a phone contact or email address you now to be the real one to confirm you are not being scammed.
- Do not answer any questions requesting for your personal information (full name, date of birth, Identity card number) from strangers who call you.
Limit the personal information you share online. If possible, avoid posting your full name, address, or phone number on public sites. An identity thief could find that information and use it to answer the security questions required to verify your identity and log in to your accounts.
- Likewise, do not confirm information read out to you such as your ID, full names, etc., to strangers in person or over the phone.
- Protect your mobile phone PIN numbers.
- Avoid using SMS-based two-factor authentication. Read more on the risks of SMS-based two-factor authentication and what you should use instead.
DO
- Hang up or ignore calls from strangers directing you to share your personal identifying information or requesting you to key in characters on your phone to perform certain tasks. If you’re unsure, call your service provider or go to their physical stores to confirm.
- Ensure that your phone SIM has an active SIM card lock.
- Limit the personal identifying information that you share online and on social meida. This includes your full name, address or phone number. A scammer could use this information to build a profile about you that allows them to answer security questions required to verify your identity and login to your accounts or initiate a SIM SWAP succesfully.
- Know the trusted lines that belong to your mobile service provider support line so as to instantly become suspicious should you receive a call from an alternate number.
- Stop using SMS-based 2FA. Instead use application-based 2-FA methods such as Google Authenticator.
What To Do If you Become a Victim of SIM SWAP Fraud
In the unfortunate event that you become a victim of a SIM SWAP fraud, here are two things you should do.
- Contact your mobile service provider immediately so that you can regain control your phone number from the scammer.
- Once you regain control of your account, change your account passwords – starting with your email account passwords
- Check your bank account, credit card, mobile money and other accounts for transactions you did not authorize. Notify the relevant bank or other institution of the fraudulent transactions to stop any further losses on your accounts.
Conclusion
If you’re still using SMS for two-factor authentication, it’s time to stop.
Consider alternative application-based methods or even physical devices such as a token or biometrics.
![]()




Pingback: 6 Risks of Public WiFi and How to Stay Safe