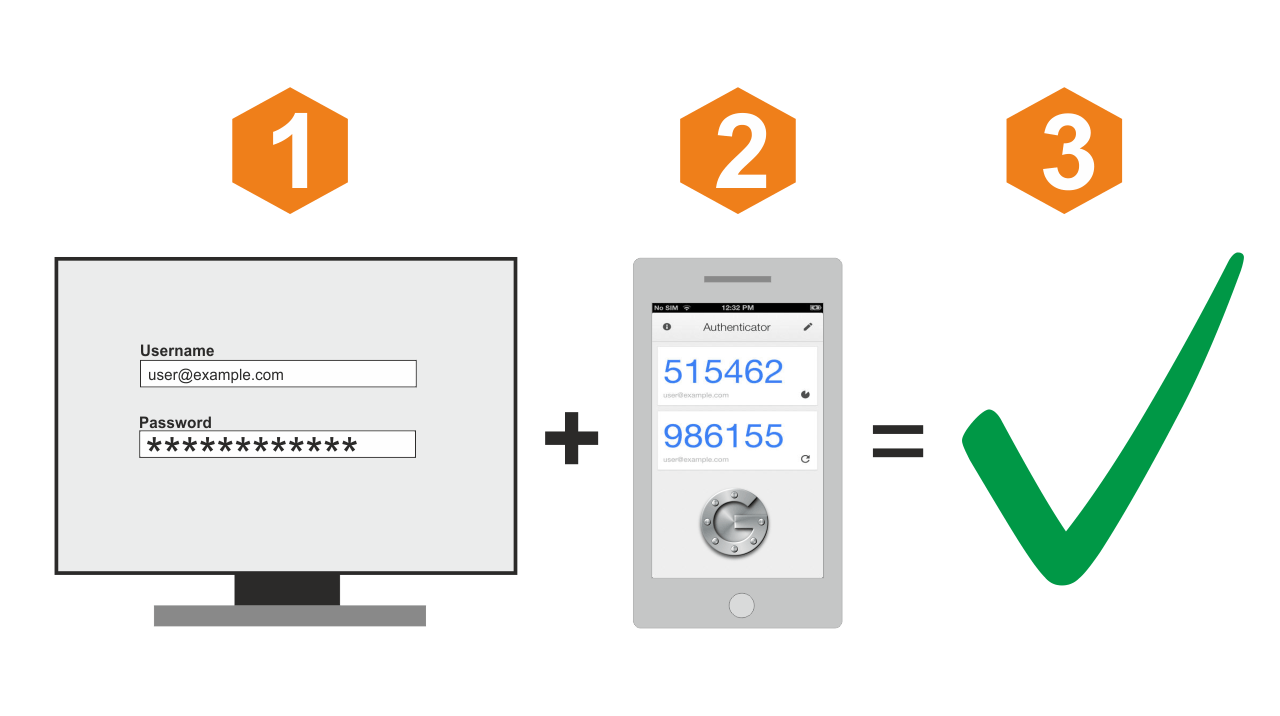
What is Email Security, and Why is It Important?
Email remains one of the most widely used forms of communication in both personal and professional settings. However, it is also a significant target for cybercriminals looking to exploit vulnerabilities.…