Phishing scam emails cotninue to be a leading attack vector in across the globe, and it is important that your entire staff recognizes the signs of a phishing email. Companies of all sizes are targets for frequent, extremely sophisticated phishing scam attacks, and it is unrealistic to expect IT and security teams to identify all phishing attacks and fight that battle alone using only technology.
While email filtering solutions can significantly minimize the risk of phishing and scam emails getting to your mailbox, sometimes, a few sophisticated ones can still make their way through.
In this article, we will discuss:
- Why scammers send you phishing emails
- Why phishing awareness is important to businesses
- 13 typical signs of a phishing email – learn the tell-tale signs of a fake or scam email, including examples.
- What more you can do if you identify a phishing email.
1. Why Scammers Send You Phishing Emails

Phishing emails are sent to:
- Create a sense of urgency to get you to engage with the scammers in order to defraud your company or get other sensitive information from you.
- Deliver malware to your computer via attachments or links.
- Redirect you to a malicious website – often, a replica of a legitimate company’s website.
- Trick you into sharing your login credentials, financial information, or other confidential information in a bid to defraud you or your company.
Now that we know why scammers send phishing emails, let’s understand why phishing awareness is important for any business.
2. Why Phishing Scam Awareness is Important to Businesses
Successful phishing attacks give attackers a foothold in corporate networks.
There are many types of phishing attacks, but in a nutshell, phishing is any type of attack by email that is designed to trick the recipient into taking a specific course of action such as clicking a link that leads to a compromised website, opening a malware-laden attachment or divulging confidential information such as intellectual property, usernames and passwords, credit card information, and so on.
While a good spam filtering solution is vital armor in the war against scam emails, on their own, email filters are not 100% effective, and consequently, not sufficient protection from all scams.
Because you (human) are the target of phishing scam emails, you must also play a role in the war against cyber criminals who are trying to compromise your company systems and data. To help in the fight against spam, you must learn how to recognize the signs of an email phishing scam to prevent yourself from becoming a victim.
Below are some tell-tale signs which, if spotted by the recipient, can prevent a scam phishing attack from being successful. But first, it is important to know the difference between a phishing scam email and a spam email.
3. The Difference Between Spam and a Phishing Scam Email

A spam email is relatively harmless. While it may be unsolicited and come from an unknown email address or look generally unusual, these types of emails usually are trying to sell you on something. For example, a spam email could aim to entice you into subscribing to something, purchasing an item or read an unsolicited newsletter.
In contrast, phishing emails are designed to be dangerous as described in section 1 above. Below are common signs that can help you recognize that an email is not as genuine as it appears to be and is potentially a phishing or scam email.
4. 13 Typical Signs of a Phishing Scam Email
Although an email similar to those described here will not always be a phishing email, you should instinctively be on high alert when you notice any of the following signs.
i. Spelling, Grammatical and Punctuation Errors
One of the more typical signs of a scam email is spelling and grammatical errors. Most reputable companies follow strict email etiquette and editorial standards. While some typing errors may happen occasionally, it’s uncommon to see several glaring errors in a single email. Therefore, if you see multiple errors, this is a red flag you should not ignore. See the example below.
Re: Thank you for your purchase
Dear Customer,
Your Apple ID has just been used to buy Race Game from the App Store from unknwn device
Date: Tuesday 10 July 2019
Browser: Chrom
Operate system: 12.1
If you did not authoriz purchase. please fill attached form before 11 July 2019 to cancel order
ii. Links in the body of the email that redirect to unexpected sites
If a link in the body of an email takes you to a site different from that written on the link, this is a red flag. Scammers can include text that looks like it will take you to a genuine website. However, the actual hyperlinks they embed on this text take you to a phishing or malicious site instead.
Example: You get an email that looks like it’s coming from PayPal. It’s warning you about an unauthorized login attempt and asking you to change the password to protect your account. There is a link given to change your password: https://www.paypal.com/account/passwordChange. You think it’s safe as the link looks legit. However, when you click on it, you’ll be redirected to some scam website that appears legitimate because they use PayPal’s site design, colors, fonts, and logo. Here, the fake website will try to trick you into typing your login credentials or divulge other confidential information.
To be safe, you can either:
- Compare with previous emails received from the sender that the sender’s email addresses match, or,
- For a link embedded in the email, hover your cursor over it to verify what ‘pops up’. If the email is allegedly from Amazon, but the link domain does not include “amazon.com,” that’s a huge red flag. If the domain names don’t match, don’t click.
Some links lead users to a malware-laden website that auto-downloads malware onto your device without your knowledge. Sometimes, malicious redirects are also concealed in the Unsubscribe button.
To confirm if a link is safe without clicking on it, hover your cursor over it to display the real URL. If the text in the pop-up URL differs from what displays in the linked text (as in the example below), it’s likely a malicious link so do not click on it!
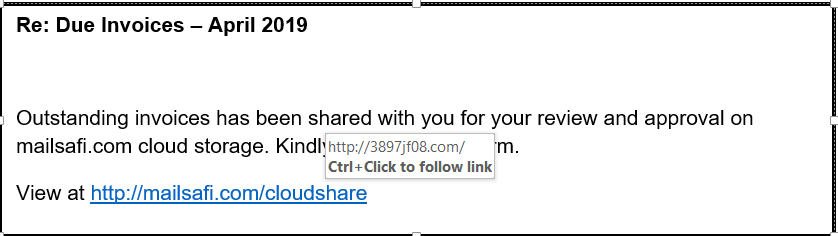
Another URL Inspection Tip
If any of the links in your message uses a URL shortened (links that start with tinyurl, bit.ly, goo.gl, is.gd, t.co, etc.), you can see the expanded URL by using this website: getlinkinfo.com
In the past, people would shorten URLs to make links consume less space and look more professional. Unfortunately, nowadays, scammers are also using URL-shorting tools to conceal their original malicious links.
iii. Threats or a Sense of Urgency
Scammers like to create a sense of urgency by imposing time limits to urge or even demand immediate action from you. Always treat emails that threaten negative consequences for failing to do xyz with skepticism. The scammer hopes that by reading the email in haste, you will not scrutinize the content of the email thoroughly. Reading in haste means you are likely to overlook other inconsistencies associated with phishing campaigns.
Re: Account Verification Required!
From: MailSafi <support@mailsafii.com>
Dear Valued Customer,
We recently have traced various computers attempting to log into your email account with multiple password failures. For your security, we need you to confirm your account details by 6 July 2020. If this is not done, we will be forced to lock your account for security reasons.
To confirm your account, click here.
Regards,
Support
iv. Request for Credentials, Payment Information or Other Personal Details
Beware of any email asking you to update your account information and providing a link to do so. This may be a phishing email. One of the more sophisticated phishing emails is when an attacker creates a fake landing page that recipients are directed to by a link in an official-looking email. The fake landing page will have a login box for you to type in your credentials or other confidential information. Sometimes, these emails and fake landing pages may even have the logo and other identifying information of a business you know. However, if you click on the link (Don’t!), it will lead you to a dummy site designed to steal your credentials and/or other confidential information.
If the email was unexpected, visit the website from which the email has supposedly come by typing in the URL – rather than clicking on any link in the body of the email – to avoid typing in your login credentials on the fake site or making a payment to the attacker.
v. Suspicious Attachments
A good rule of thumb when it comes to email attachments is to ask yourself: “Did I request for this information?”
If you receive an email with an attachment from an unknown source or if you did not request or expect to receive a file from the sender of the email, be cautious as cybercriminals will often send emails with attachments to trick you into downloading their malicious executables. These attachments could come in many forms, including:
- Request for quotation
- Receipts for payment
- Photos or other graphics
- Pricing sheets
- Invoice documents
If you receive an email with a .zip, .exe, .scr, or other unfamiliar extension, flag the file to be virus-and-malware scanned before clicking on it to open. Others still appear as simple spreadsheets, Word, or PDF documents.
Since Microsoft and Adobe added the ability for Word documents and PDFs to work like executables via scripting and macros, document-based malware sent over emails have become increasingly common. Unfortunately, once downloaded, some of these malwares have the ability to spread to other documents in the system. Should this happen, other legitimate documents sent from the same workstation can spread the virus further within the network, to clients, and other business associates. If sent externally, it has the potential of getting your domain blacklisted on for sending emails with malicious content.
Re: February Invoice #09808
Attachment: Internet bill - invoice09808.doc
Attached is invoice for Feb. Please make payment before 12 February 2018 to avoid disconnection.
Thanks
If in doubt about whether an email or attachment is legitimate, contact the sender directly – preferably on phone using contact sources you trust such as the company’s website or one you already had stored before. Never use the contact information that’s listed in an email that is questionable!
vi. An Unusual Tone or Greeting
The first thing that should arouse your suspicion when reading a phishing email is if the language seems odd, unusual, or unfamiliar. For instance, a colleague is suddenly over-familiar or a little more formal than they ordinarily are.
For example, if I were to receive an email from MailSafi’s CTO that began with “Dear Joy,” that would immediately raise a red flag. In all of our communication, he has never begun an email with that greeting so it would feel unusual. If a message appears strange, it’s worth scrutinizing it in more detail for other signs that it may be a phishing scam email.
vii. Unusual Request
If an email asks you to do something that is out of the norm, then that too is a red flag. For instance, if an email claims to be from the ICT department and asks you to install a certain program or contains a link for you to click in order to upgrade or patch your system, yet ordinarily, this type of activity is managed by the ICT department, that should be a big indicator that you are most likely reading a phishing email and you should not to follow the instructions.
viii. Pushy or Suspicious Language
There are many subjects that elicit emotional responses from email recipients. Hackers know this and will use email subjects that will spur you to take action you ordinarily wouldn’t, without stopping to inspect or investigate the emails properly. Scammers will try to trigger emotional responses like anger, shock, empathy, panic, curiosity, etc. Here are some example subject lines of such emails:
- COVID-19 fundraising campaign for Slum Dwellers
- An unbelievable deal!
- You won!
- Sales job vacancy
- Unauthorized access to your account
- Your purchase on Amazon is complete
ix. You Did Not Initiate the Conversation
Because scam emails are unsolicited, an often used tactic is to inform you that you have won a prize, will qualify for a prize if you reply to the email, or you will get a discount or discount code by clicking on a link or opening a certain attachment.
In cases where you did not initiate the conversation, e.g., by opting in to receive marketing material or newsletters, etc., there is a high likelihood that the email is malicious.
x. Uncommon Uses of the Email Bcc Field
In some emails, you will see your email address listed in the Bcc field instead of the recipient field. While there’s technically nothing wrong with this, it is uncommon for organizations to use the Bcc field when communicating with customers. No genuine company will send a blind carbon copy email asking you to verify your account information or to requesting you to download transaction receipts. They will reach out to you directly.
So, if you see your email address in the Bcc field instead of in front of “To:” or “Send To:” it’s a good indicator that the email is a fake.
Let’s consider the example phishing email in the screenshot below. Check out how the sender lists my email address in the Bcc column instead of the recipient (To:) field. Also, see how smart the sender is by including “@amazon.com” as part of the sender’s display email address to deceive the recipient.
Re: Amazon Billing Info #278797 – Action Required – Waiting verification
From: billing-alert@amazon.com <mammoth@gmail.com>
To: billing-alert@amazon.com
Bcc: jill@asdesk.com
Account ID: #9089A879
This is a system generated email. Please do not reply, thanks.
Click to view your statement.pdf
xi. Inspect the Email Header Info to Verify Whether the Sender’s Email Address is Legit
Genuine organizations typically send emails from email addresses containing the company’s domain name after the “@” symbol. For example, xyz@absa.com, xyz@amazon.com, abc@jpmorgan.com, etc. The company’s domain is what comes after the “@” sign. To get such an email address, you must own the domain name. Alternatively, an authorized person from the company must create one for you.
If you get an email claiming to be from a well-known organization, here’s how you can easily tell if the email is not genuine:
- The sender’s email is coming from a free domain email addresses such as Gmail, Hotmail, Yahoo, AOL, etc. Related article: 6 reasons not to use free web-based email for your business
- The email is sent from an unknown domain name.
- The sender’s name and the name in the email address don’t match.
For example, if the sender claims that email is from ABSA, the sender’s email address must have @absa.com in it. If the sender’s email address ends with “@gmail.com” or some unusual domain name after @, this is a glaring red flag.
Wednesday, 15 Jan, 2017 10:45:16 AM
Subject: Notification: Inbox Space Running Out
From: Administrator <absabank@gmail.com>
To: Peter Simba <peter.simba@kachooks.com>
Kachooks.com Administrator
Your mailbox is almost 100% full. Once you reach the limit, no more emails will be delivered to your mailbox.
Login here to request for additional space.
From the illustration above, a legit email would likely be coming from @absa.com not from a Gmail account.
Below is another example of a phishing scam email. Here, the cybercriminal impersonates one of your HR staff, William Paul. However, the email address is not correct – typically, unrelated to the company in question.
Tuesday, 15 Jan, 2018 11:17:18 AM
Subject: Request for payroll and bills authorization
From: William Paul <william@redhills.com>
To: Kate Williams
Kindly log in here to review and approve this month’s payroll and bills. I will appreciate your quick response to avoid delaying payments
Kind regards,
William
Cybercriminals hope that the recipient will see the name (William Paul in this example) and forget to double-check the email address william@redhills.com
Carefully scan email headers for deceptive domains and spelling differences in email addresses.
Sophisticated attackers are smart enough to not use a generic free email address. Instead, they purchase domain names that look similar to the genuine company’s domain that they wish to masquerade as.
Below are some examples of how scammers may use deceptive (look-a-like) domains names:
| The trick | Original Domain | Deceptive (look-a-like)domain |
| Replace “S” with “5“ | absa.com | ab5a.com |
| Replace “m” with “rn“ | safaricom.com | safaricorn.com |
| Replace “L” with “1” | wallmart.com | wal1mart.com |
| Replace “O” with “0” | carrefour.com | carref0ur.com |
| Add extra letters, words or symbols | amazon.com ebay.com mtn.com | amazon-online.com ebaysupport.com mttn.com |
Some of these subtle differences to the domain names may be difficult to recognize. Therefore, it is important that you always scrutinize the sender’s email address with extra caution.
xii. Short and Sweet
While many phishing emails will be packaged with details designed to offer false security, some are also scanty in information, hoping to cash in on their ambiguity. For instance, a scammer that spoofs an email from Philip at an organization that is a regular supplier emailing the company once or twice weekly, may have the vague message, “Please find attached as earlier requested” and an attachment titled ‘Additional information’ in hopes they’ll get lucky.
xiii. Be Vigilant – Even If the Email is From a Known Email Address
You may receive an unsolicited or unexpected email from a known email address. It may be from a colleague, relative or friend, but it may look or feel “off”. There’s no specific science to define what “off” means, just use your instincts. For example, the email may ask you to:
- Urgently transfer money to help them as they are stuck.
- Follow a certain link to a website to get an unbelievable (unrealistic) deal.
- Donate money to some unknown charity.
- Reply with your phone number, some files or personal information such as banking info.
- Download a software, attachment, or a media file.
If you get such an email, this is another time when you should reach out to the sender personally (even if the email is from a legit email address) via phone before taking any actions suggested in the email. Your loved one’s email account might be compromised, and they have no clue about it!
Clicking on links or attachments in such emails could cause you to download malware you’re your device or computer. Some malware is designed to corrupt a users’ devices and send phishing emails on their behalf to other victims. These types of malware delete the emails from the sent folder, and the victims remain unaware of such compromise.
5. What to Do If You Identify a Phishing Scam Email
Recognizing a phishing or scam email is a great first step in aiding your business fight scam. When you do identify a phishing email, ignoring such fake emails isn’t enough. You should also:
- Block the sender using settings in your email client or mailbox. You can do this by clicking on options for “Block sender” or “Report as spam”. If you don’t want to open the email, you can right-click on it in your inbox. In the drop-down menu in Gmail, for example, go to Move To and click on Spam.
- Delete phishing emails to avoid accidentally clicking on them in future.
- Call sender to confirm. If in doubt whether an email you have received is a phishing email, call the sender (if it claims to be from someone or a company you know) and verify first.
- Report the phishing email to your incident response team. As the old adage goes, “See something, say something.” In any organization, if you are receiving a phishing email, chances are that others are as well. If you receive a phishing email from someone impersonating a company you know, forward the email to that company’s official customer support to let them know.
It becomes the responsibility of your incident response team to scrutinize these reports to ascertain there are no false positives. Because these alerts may be many, the incident response team needs to prioritize alerts received from users who have a history of accurately flagging phishing attacks. These employee-sourced, prioritized reports provide the incident response team with information to mitigate the risk of phishing threats that have not been captured by email filtering systems.
In Conclusion…
If you’re a company or business, all it takes is one user falling pretty to a phishing attempt to compromise your entire network. It is therefore important to promote phishing awareness and condition employees to report signs of a phishing email to your internal incident report teams. Companies need to regularly educate all staff on cyber security best practices because your security is only as strong as your weakest link. Teach employees how to recognize and avoid phishing scams, create strong passwords, and avoid common cyber threats online. Educating your staff about cyber security risks and best practices empowers them and builds a culture of personal accountability within an organization in the fight against spam.
Get in touch with us to discuss how we can help your organization in this regard through our cyber security training
Although no email filtering solution can be 100% effective, any business email system without an email filtering solution is highly vulnerable, if not unusable. It is important to use technology to stop as much spam, viruses, malware, phishing attacks and other advanced email threats as you can to protect your network from the many possible risks. In this way, you will offer your users, network and business an additional layer of protection.
If you don’t already have an email filtering solution in place as a first line of defence, sign up today for MailSafi Email Security and watch the volume of spam and phishing emails coming to your mailbox decrease drastically!
![]()





Pingback: The Russia Ukraine Conflict - Cybersecurity Threats | Kaluari