Especially for business email, using two-factor authentication (2FA) is the right thing to do, but you put yourself at risk by getting codes over SMS (text messages). We explain why.
Two-factor authentication (2FA) brings an added layer of security that passwords alone can’t provide. When it comes to email, requiring an extra step for a user to prove their identity reduces the chance of an unauthorized person gaining access to your email account.
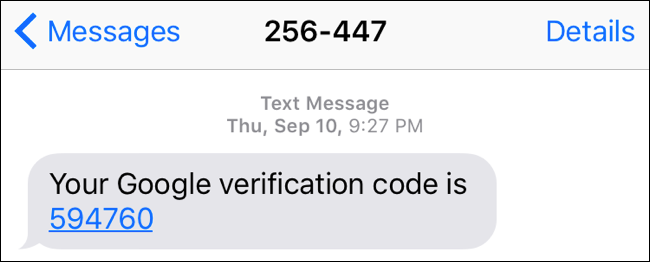
One of the most common methods of 2FA is SMS (text messages). However, while popular, using SMS for authentication is actually not a great idea. Hackers have several tools that can intercept, phish, and spoof SMS, therefore, making SMS authentication a less secure medium.
1. How hackers intercept SMS
It is a great idea to add 2FA to email access, especially webmail access, to increase email security. Password attacks are becoming more sophisticated, and even complex passwords can be cracked. Therefore, requiring additional authentication for accessing email will ensure better protection.
But after taking that additional security step, why use an insecure form of communication for that verification? After all, SMS (text) messages are based on telephone networks. The first hackers were a bunch of folks who were looking for cool ways to get around phone networks. Intercepting SMS is, therefore, a walk-in-the-park for many hackers.
Studies have found that the main issue with using SMS in 2FA is that the mobile service providers themselves and their network are vulnerable to phishing, spoofing, and social engineering.
Here are some examples:-
- A hacker can hijack your phone number by convincing your mobile service provider (through social engineering) to transfer/port it to another SIM card (SIM swap). In most cases, this could be as easy as knowing your phone number and providing your National Identity Card or Social Security Number – data that tends to be easily leaked by government agencies, financial institutions, or other corporates. Once a hacker has redirected your phone number, they no longer need your physical phone to gain access to your 2FA codes. Before you notice, the hacker will have already accessed your email.
- If you sync SMS messages with your computer, laptop, or tablet, a hacker could access SMS codes by stealing any of these devices.
- A hacker can intercept an SMS message due to weaknesses in the mobile service providers’ systems. In what’s called an SS7 attack, a hacker can spy via the cell phone system, listen to calls, intercept SMS messages, and see your phone location.
- It is easy to spoof. It is very easy to spoof an SMS message. There is no SSL or certificate to verify where it really came from.
- Unfortunately, you cannot control phishing at the mobile service providers’ company.
- If you know some basic information about the person, you can get the PIN changed. Spoofing may actually be combined with phishing to gain access. This process allows hackers to falsify a message to appear like it’s coming from a legitimate source. The message will alert the victim that they need to reply with the security code. At the same time, the hacker will trigger a login 2FA request. If the victim replies with that code, the hacker can use it to gain access.
2. Alternatives to SMS for 2FA
While it’s best to skip 2FA if SMS is the only option, this doesn’t solve the reason for adding 2FA in the first place. To prevent brute force and other attacks targeting password-only authentication, some form of 2FA is needed.
2.1 Hardware authentication for 2FA
Hardware authentication relies on a dedicated physical device to grant access. Users will also have to input a random token code generated by the device along with their password. Logins will fail without the code. Some providers of hardware authentication include RSA SecurID and Thales SafeNet.

The physical nature of this method does have the potential for devices to be lost and stolen. But it does address many of the security issues inherent to SMS-based 2FA.
2.2 App authentication for 2FA
App authentication is, essentially, the same principle as hardware authentication. However, instead of requiring a physical device, token codes are generated with a mobile application. Some popular authentication apps are Google Authenticator, Microsoft Authenticator, or Authy. RSA now also offers their SecurID authenticator as an app.
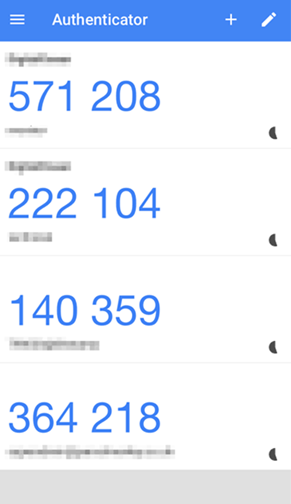
It may seem counterintuitive to recommend authentication based on a mobile device. However, the app is not relying on SMS or the phone network for authentication, eliminating the inherent flaws in SMS-based 2FA.
An authentication app has the advantage of not needing to rely on your carrier. These apps can be downloaded from any Android, Windows, or iOS phone. Codes expire quickly, usually after about 30 seconds. Since an authentication app doesn’t need your carrier to transmit codes, they will stay with the app even if a hacker manages to move your number to a new phone.
Although using an authentication app requires a little extra setup initially, in the long run, it offers better protection than SMS. MailSafi uses Google Authenticator for 2FA.
2.3 Biometric authentication
Using a thumbprint or facial recognition is becoming more commonplace. Biometric authentication relies on a unique physical trait of an individual and is therefore very accurate in authenticating the end user.
2.4 IP-based authentication
This method checks the user’s IP address when logging in. You can block access to specific IP addresses suspected to be malicious, or simply only allow logins from known IP addresses and ranges. IP-based authentication can be used in conjunction with other forms to add another layer of protection.
2.5 GPS authentication
This method uses GPS data as an added level of security that allows banks or other payment providers to use the geolocation information gained from the app to determine whether a transaction aligns with the location of the individual’s mobile.
3. If the only option I have is SMS for 2FA, should I use it?
Yes, if it’s the only option available for 2FA, just use it!
Although we have made a case against using SMS for 2FA, using SMS is better than not using 2FA at all. When you don’t use two-factor authentication, a hacker only needs to obtain, crack, or guess your password to sign into your email account.
When you use two-factor authentication with SMS, someone will need to acquire both your password and gain access to your SMS messages to gain access to your account. For this reason, SMS is more secure than nothing at all.
4. Summary
Relying on SMS for authentication actually introduces a layer of risk to your email security. Alternatives to SMS authentication are app authentication, hardware authentication, biometric authentication, GPS authentication, or IP-based authentication.
That said, if SMS is your only option for 2FA, please go ahead and use it, but this should be even more reason to pair it with a good password strategy.
While stronger 2FA options are recommended, they are not a replacement for a good password strategy. Think about it like you would your home security: A strong burglarproof front door is great, but it won’t matter if you leave the key under the doormat.
![]()




Pingback: How SIM-SWAP Fraud Affects Your SMS-based 2-FA | MailSafi
Pingback: 6 Risks of Public WiFi and How to Stay Safe