What is phishing? Phishing (pronounced fishing) is trying to gather personal information using deceptive emails and websites.
Phishing is one of the oldest types of cyberattacks dating back to the 1990s. It is also still one of the most widespread and malicious attacks. Indeed, Verizon’s 2020 Data Breach Investigations Report finds that phishing is the top threat action associated with breaches.
Phishing messages and techniques have become increasingly sophisticated over the years and perpetrators are getting much better at it thanks to well-produced, off-the-shelf tools and templates.
1. Phishing Defined
As the name suggests, phishing (fishing) is an analogy of a fisherman throwing a hook with bait and hoping the fish bite. In this case, the cyber attacker hopes his target (possibly you) falls for the trick.
Phishing is a cyberattack that uses disguised email as a weapon. What really distinguishes phishing is the form the message takes. The attackers masquerade as a trusted person or company the victim might do business with. The aim is to trick the email recipient into either disclosing sensitive information, downloading an attachment, or transferring funds.
2. Characteristics of Phishing
While there are different types of phishing, the common characteristic among phishing attacks is disguise. Cyber attackers make their email address looks like it’s coming from someone else (spoofing). They then set up fake websites that look like ones their target trusts.
Generally, a phishing campaign will try to get its victim to do one of three things. Either divulge sensitive information, launch fraudulent transactions, or download malware onto their computers.
Divulge sensitive information. These messages aim to trick you into revealing important data. This is data such as passwords, identity card information, date of birth, bank account and credit card details, etc.
Most often, a username and password that the attacker can use to breach your system or account. This is done by sending emails that appear to be messages from financial institutions such as banks. Although the attackers may not know where you bank, by sending the email message to millions of people (spamming), the attacker is certain that some of the recipients will be customers of that bank.
Clicking on a link in such a message will often direct you to a malicious site designed to resemble the bank’s site. The attackers hope that you will key in your username and password here. Once you do, they can capture these details and use them to access your bank account
Launch fraudulent transactions. The attacker’s email appears to be from a legitimate source and gives instructions to transfer funds to an account.
Download malware. These types of phishing emails aim to get you to infect your computer with malware. They might send staff in the HR department an attachment that claims to be a job seeker’s CV, for example. The attachment is often a .zip file or Word document embedded with malicious code.
3. Types of Phishing Emails
According to Proofpoint’s 2020 State of the Phish report, 65% of US organizations experienced a successful phishing attack in 2019. This speaks to both the sophistication of attackers and the need for equally sophisticated security awareness training. Add in the fact that not all phishing scams work the same way. Some are generic email blasts. Others are carefully crafted to target a specific person, making it harder to train users to identify suspicious messages.
Let’s look at the different types of phishing attacks and how to recognize them.
i. Phishing: Mass-market emails
Mass-market phishing is the most common form of phishing. It is a general, mass-mailed type, where someone sends an email pretending to be someone else and tries to trick the recipient into doing something, usually logging into a website or downloading malware. Attacks frequently rely on email spoofing. Here, the From field is forged to make the message appear as if it were sent by a trusted sender.
However, phishing attacks don’t always look like a warning message from PayPal about passwords expiring, or an Office 365 email about storage quotas. Some are crafted to specifically target organizations and individuals.
Here is an example of a Phishing email captured by MailSafi spam filters.
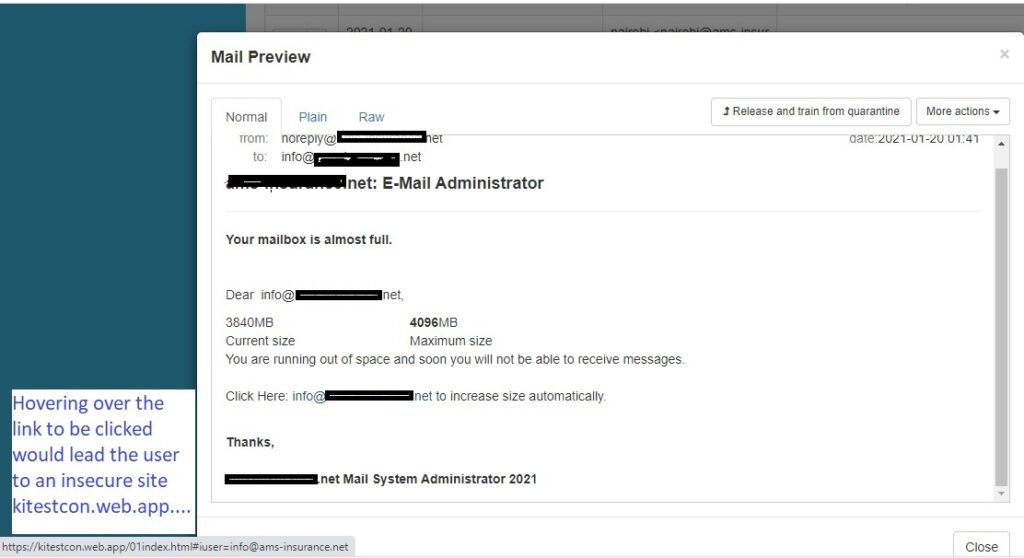
ii. Spear phishing: Targeting just a handful
Spear phishing refers to when cyber attackers try to craft a message targeted to a specific individual. (The image is of a fisherman aiming for one specific fish, rather than just casting a baited hook in the water to see who bites). Instead of trying to get banking credentials for 1,000 consumers, the attacker may find it more worthwhile to target just 10 businesses.
Spear phishing attacks are extremely successful because the attackers spend a lot of time crafting information specific to the recipient. They may gather information about their target from sites such as LinkedIn. Or, they may reference a conference the recipient may have attended or send a malicious attachment where the filename references a topic the recipient is interested in. They then use spoofed addresses to send emails that appear like they’re coming from co-workers.
Example: The spear phisher might target someone in the finance department and pretend to be the victim’s manager urgently requesting a large money transfer.
Also, see another example of a spear-phishing attack targeted at a member of our staff at MailSafi.
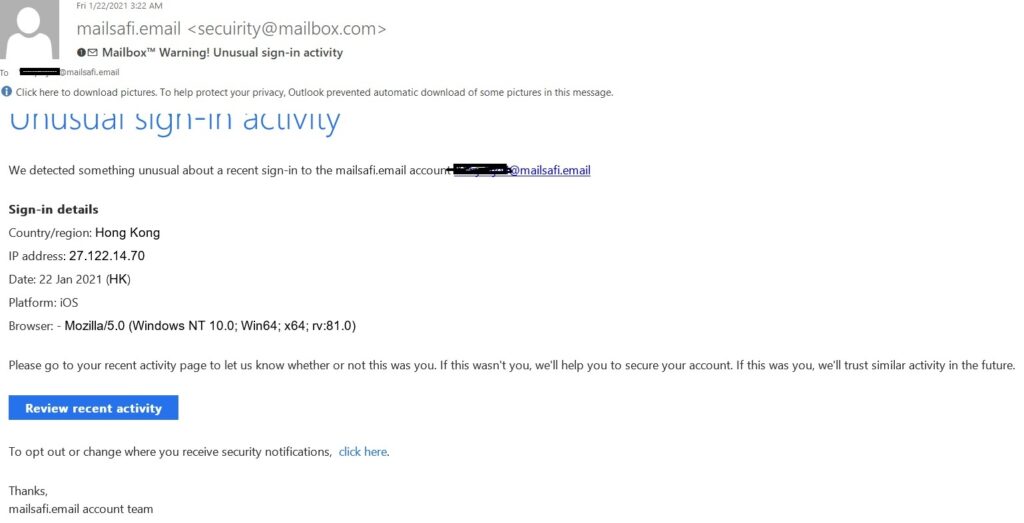
iii. Whaling: Targeting the big fish (top executives)
Whale phishing, or whaling, is a type of spear phishing aimed at the very big fish — top executives, CEOs, or other high-value targets. A successful whaling attack is likely to be more lucrative because the stolen information may be more valuable than that from a regular employee.
Whaling needs additional research because the attacker needs to know who the intended victim communicates with and the kind of discussions they have.
Example:
- A scammer may target company board members because while they may have a high level of authority within a company, they aren’t full-time employees, and therefore, they often use personal email addresses for business-related correspondence. Personal email addresses may lack the level of protection offered by corporate email.
- Emails that reference customer complaints, legal subpoenas, or even a problem in the executive suite.
iv. Business Email Compromise (BEC): Impersonation of finance officers/CEOs
In BEC, scammers pretend to be key individuals in finance departments or CEO/MDs. By impersonating financial officers and CEOs, these criminals attempt to trick victims into initiating money transfers into unauthorized accounts.
Here’s how it works:
- First the cyber criminals compromise the email account of a senior executive or financial officer by exploiting an existing infection or via a spear phishing attack.
- The attacker then hangs around monitoring the executive’s email activity for a period of time to learn about processes and procedures within the company.
- Then the attack. Typically in the form of a false email that looks like it has come from the compromised executive’s account being sent to someone who is a regular recipient. The email appears to be important and urgent, and it requests that the recipient transfer funds to an external or unfamiliar bank account. If successful, the money ultimately lands in the attacker’s bank account.
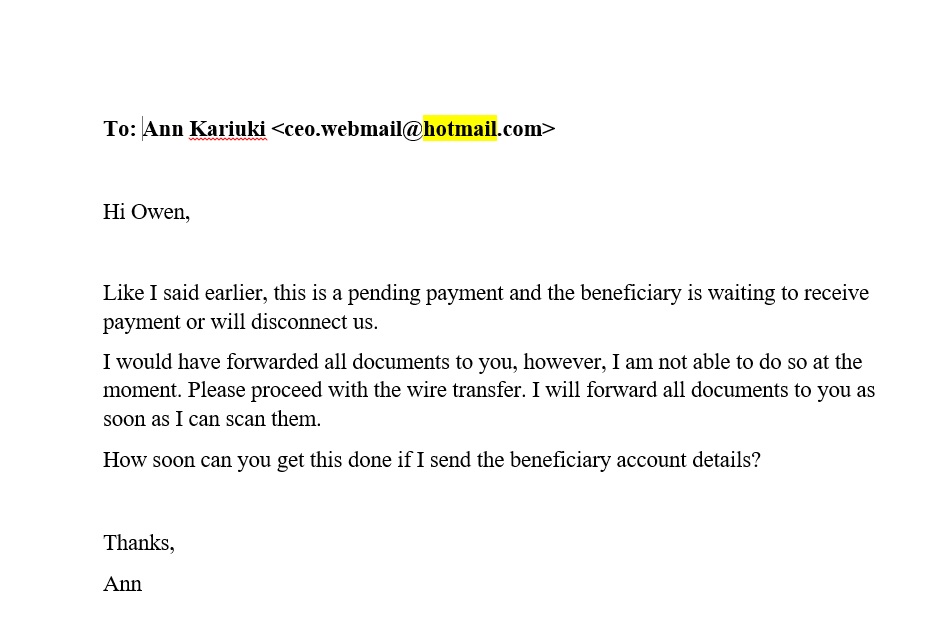
According to the Anti-Phishing Working Group’s Phishing Activity Trends Report for Q3 2020, the number of phishing attacks had grown since Q2 2020 and the average amount requested during wire transfer BEC attacks in Q3 2020 was $48,000.
v. Clone Phishing: An almost identical copy
In clone phishing, the attacker may either:
- Create a cloned website with a spoofed domain to trick the victim, or
- Craft a nearly identical replica of a legitimate email message to trick the victim into thinking it is real.
In the case of the cloned email, the email is then sent from an email address that closely resembles the legitimate sender. While the body of the message may look the same as a previous message, the attachment or the link in the message has been swapped out with a malicious one. The attacker will usually try to explain the reason he is resending the message, or an updated version, such as “Sorry, sent the wrong attachment earlier. Please refer to this one instead.”
This attack relies on a message previous legitimate message seen by the recipient. This undoubtedly makes it more likely that the email recipient will fall for the attack.
An attacker who has already infected one user may use this technique against another person who also received the message that is being cloned.
vi. Snowshoeing: Spreading poisonous messages
Snowshoeing, or “hit-and-run” spam, requires attackers to push out messages via multiple domains and IP addresses. By doing this reputation or volume-based spam filtering technologies will not recognize and block them immediately because each IP address/domain sends out only a low volume of messages.
Some of the messages make it to the targets’ email inboxes before the spam filters learn to block them.
4. Other types of Phishing
There are also other types of phishing attacks, although these are not sent via email. These are the wangiri scam (phone), vishing (phone), and smishing (SMS).
Vishing: Phishing over the phone
Vishing stands for “voice phishing” and it entails the use of the phone. Typically, the victim receives a call with a voice message disguised as a communication from a financial institution.
Example: The voice message might ask the recipient to call a number and enter their account information or PIN for security verification. What the target may not know is that the phone number they call actually goes straight to the attacker via a voice-over-IP (VOIP) service.
In a sophisticated vishing scam in 2019, criminals called victims pretending to be Apple tech support and providing users with a number to call to resolve the “security problem.” Like the old Windows tech support scam, these scams took advantage of user fears of their devices getting hacked.
The Wangiri Scam
Have you ever received a call from an unknown international number that only rang once? Did you return that missed call? If you have, the chances are that you lost money.
The term Wangiri is Japanese for “one (ring) and cut.” As the name implies the scam involves receiving missed calls from international numbers you don’t recognize on a mobile/landline phone. The fraudsters generating the calls rely on human’s innate curiosity. They hope that their expensive international numbers will be called back so that they can profit.
Many people will instinctively return a missed call, even from a mysterious international number. Returning the call will lead to the victim being ripped off as the call will be re-routed to a premium rate number overseas. The victim is billed exorbitantly for listening to pre-recorded messages.
If you receive a missed call from an unknown number, do not return the call.
Smishing: Phishing via text message
Smishing, a combination of “phishing” and “SMS” is a cyberattack that uses misleading text messages to deceive victims. The goal is to trick you into believing that a message has arrived from a trusted person or organization, and then convincing you to take certain action that gives the attacker more information about you such as your online banking login credentials or access to your mobile device.
Smishing is on the rise because people are more likely to read and respond to text messages than email: 98% of text messages are read and 45% are responded to, while those for email are 20% and 6%, respectively. Users are also often less vigilant on their phones than on their computers, and most often, personal devices lack the type of security available on corporate PCs.
Hailstorm campaigns work the same as snowshoe, except the messages are sent out over an extremely short time span. Some hailstorm attacks end just as the anti-spam tools catch on and update the filters to block future messages. Unfortunately, by the time the spam filtering tools are updated, the attackers have already moved on to the next campaign.
5. Why Cybersecurity Awareness is Valuable in Reducing Impact of Phishing Attacks
Some companies regularly remind users to beware of phishing, however, many users don’t really know how to recognize phishing scams. Also, humans generally tend to be bad at recognizing scams.
Traditional email security tools (such as spam filters) are not sufficient defense against some forms of phishing. This is because they are not 100% full-proof. Therefore, organizations need to appreciate the importance of cyber awareness training and campaigns to ensure staff is equipped with skills to aid in the fight against cyber attackers.
Typically, while a reasonably savvy user may be able to appreciate that clicking on a link in a suspicious email could result in a download of malware or escalate to gathering more sensitive information from you, most end users do not understand the impact of falling for a phishing attack.
Less cyber-aware users may think nothing would happen or wind up with spam advertisements and pop-ups. Only the more cyber aware users can associate potential damage such as credential theft and account compromise to suspicious emails. This risk assessment gap makes it more difficult for users to grasp the seriousness of recognizing malicious messages.
Organizations need to consider existing internal or external cybersecurity awareness training or campaigns to ensure staff is equipped to recognize different types of attacks.
MailSafi can help you jump start your fight against phishing with a world-class spam filtering solution and support your cybersecurity awareness efforts through our cybersecurity awareness training program.
![]()





Pingback: Scam alert: Scammer Extorts Site Owners Using Threats | MailSafi
Pingback: Phishing Scam Email Signs You Must Know | MailSafi 2021
Pingback: Cracking the Code: How to Protect Your Emails from Sneaky Security Threats » The MailSafi Blog
Pingback: The Best Spam Filter for Business – Key Factors to Consider » The MailSafi Blog
Pingback: Email Spam and Spam Filtering: What it means for Business | MailSafi