![]()
Related posts:
Why Even the Best Email Filter Cannot Guarantee 100% Protection
How SIM-SWAP Fraud Affects Your SMS-based Two-Factor Authentication 2-FA
How to Recognize Signs of a Phishing Scam Email
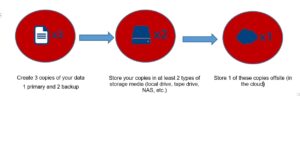
The Golden 3-2-1 Backup Rule - A Resilient Backup Strategy
Business Email Etiquette: 24 Rules You Must Know
Email Hybrids: Why They're Important for Businesses